SAST
Security
Intelligent Static Analysis Security Testing (SAST) with Code Reviews

In today's digital landscape, ensuring the security of software applications is paramount. One crucial method for achieving this is through Static Analysis Security Testing (SAST), a highly automated process that analyzes source code to identify potential security vulnerabilities. This blog will delve into what SAST is, its importance in the software development lifecycle, and how it complements code reviews to enhance application security.
What is Static Analysis Security Testing (SAST)?
SAST is a white-box testing technique that examines an application's source code, bytecode, or binary code without executing it. It uses static code analysis methods such as data flow analysis, control flow analysis, and syntactic pattern matching to detect vulnerabilities like SQL injections, cross-site scripting (XSS), and buffer overflows. SAST tools integrate with development environments, version control systems, and continuous integration/continuous deployment (CI/CD) pipelines to provide early feedback on security issues.
Steps in the SAST Process
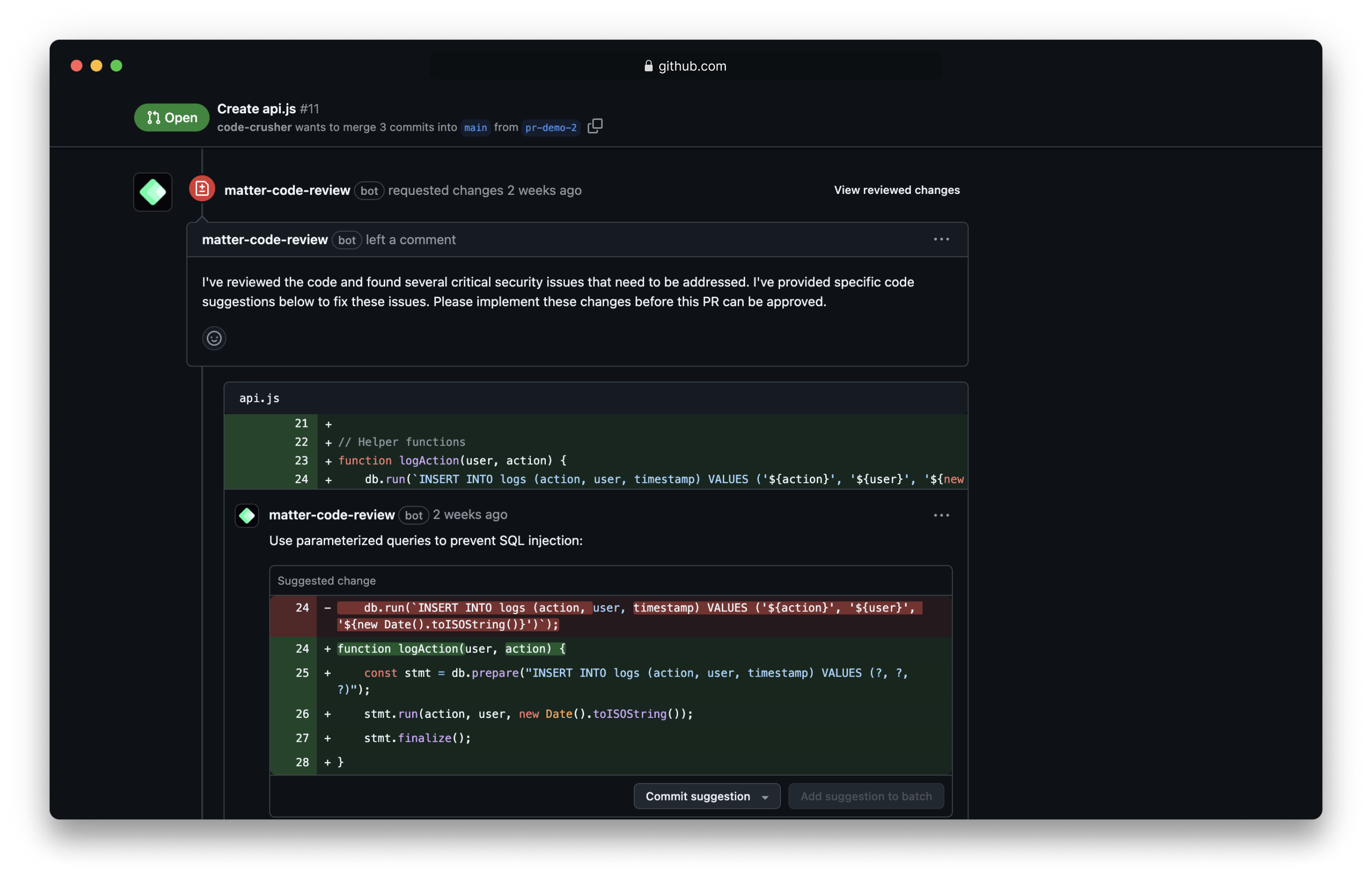
- Code Parsing: SAST tools parse the source code to create an Abstract Syntax Tree (AST), representing the code's structure and components.
- Control and Data Flow Analysis: These analyses help understand the application's behavior by identifying execution paths and tracking data movement.
- Security Rules and Policies: SAST tools apply predefined rules based on industry standards like OWASP Top Ten to identify vulnerabilities.
- Pattern Matching and Semantic Analysis: This step involves identifying coding patterns that could lead to vulnerabilities.
Importance of SAST in Catching Vulnerabilities
SAST is crucial for several reasons:
- Early Detection: By integrating SAST into the early stages of the software development lifecycle, developers can identify and fix vulnerabilities before they become costly or difficult to resolve.
- Compliance: SAST helps organizations comply with industry regulations such as PCI DSS by ensuring that applications meet security standards.
- Automation: SAST is easy to automate, allowing scans to run at any stage of the development process, which is particularly beneficial in agile environments.
SAST and Code Reviews: A Comprehensive Approach
While SAST provides automated analysis, code reviews offer a complementary, manual approach to identifying vulnerabilities. Code reviews involve developers evaluating each other's code to catch security issues that automated tools might miss. Here’s why combining SAST with code reviews is essential:
- Comprehensive Coverage: SAST tools can identify known vulnerabilities based on predefined rules, while code reviews provide a human perspective, catching issues that might not be covered by automated scans.
- Improved Coding Practices: Regular code reviews promote better coding habits and security awareness among developers, reducing the likelihood of introducing vulnerabilities in the first place.
- Efficiency: Using SAST to identify potential vulnerabilities allows developers to focus on validating and resolving these issues during code reviews, making the process more efficient.
Conclusion
Incorporating SAST into your software development process is vital for identifying and addressing security vulnerabilities early on. When combined with thorough code reviews, SAST ensures a robust security posture for applications. By leveraging both automated tools and human expertise, organizations can significantly reduce the risk of security breaches and maintain compliance with industry standards. As software complexity and cyber threats continue to evolve, integrating SAST and code reviews into your development lifecycle is not just beneficial—it's essential.
You can read more how MatterAI helps to solve SAST challenges in Pull Requests: https://docs.matterai.so/product/security-analysis
Are you looking for a way to improve your code review process? Learn more on how MatterAI helps team to solve code review challenges with AI: https://matterai.so
Share this Article:
More Articles

Fixing the $500B problem with today's AI
The key challenges that AI presents today and how we at MatterAI are working on fix them.

LLM Sampling: Engineering Deep Dive
How to tune LLMs to work for you with samplings

Prompt Engineering: The No-BS Guide to AI Communication
Understand, structure and implement prompts that gets you the best, consistant and reduced hallucination outputs.

How KV Caching Works in Large Language Models
KV caching is the optimization that solves this problem, making LLMs faster and more efficient

AI Engineering Productivity: Transforming Software Development
Artificial intelligence isn't just another tool in the developer's toolkit—it's fundamentally changing how we approach problem-solving, code creation, and system design.
Continue Reading

Fixing the $500B problem with today's AI
The key challenges that AI presents today and how we at MatterAI are working on fix them.

LLM Sampling: Engineering Deep Dive
How to tune LLMs to work for you with samplings

Prompt Engineering: The No-BS Guide to AI Communication
Understand, structure and implement prompts that gets you the best, consistant and reduced hallucination outputs.
